Cisco EIGRP authentication – what is the key? | Interface Technical Training | Interface Technical Training
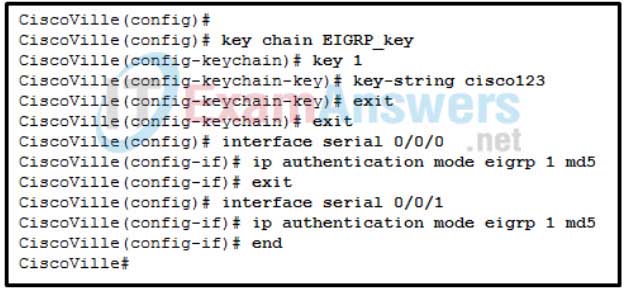
Refer to the exhibit. Router CiscoVille has been partially configured for EIGRP authentication. What is missing that would allow successful authentication between EIGRP neighbors?

15.2 EIGRP Authentication Configuration Checklist – Stuck-in-Active: Journal of an IT-Network Administrator
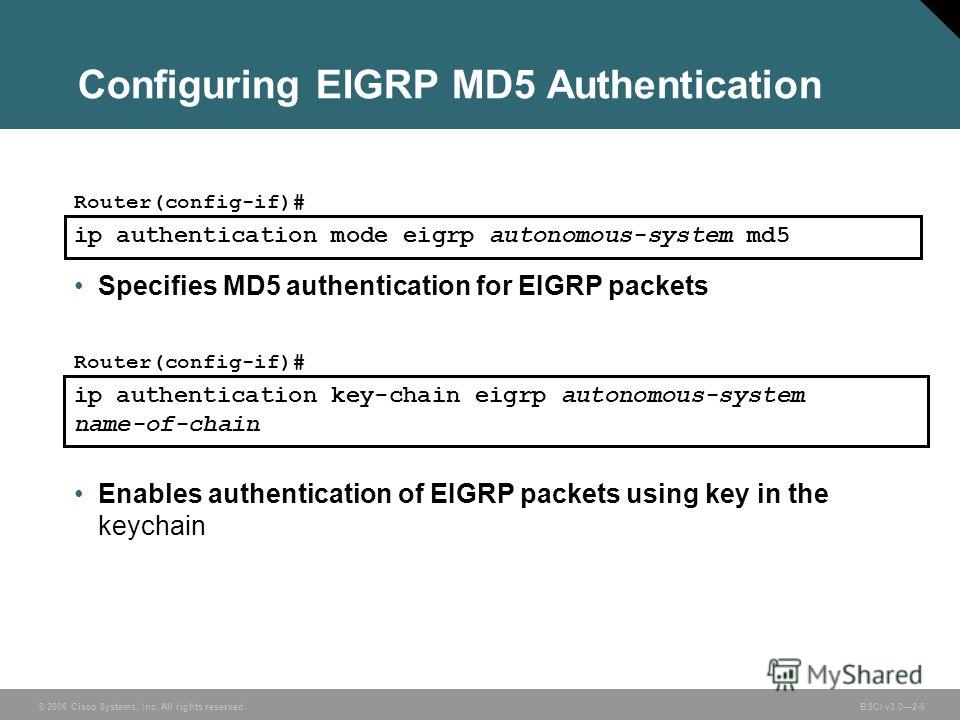
Презентация на тему: "© 2006 Cisco Systems, Inc. All rights reserved. BSCI v Configuring EIGRP Configuring EIGRP Authentication.". Скачать бесплатно и без регистрации.

Cisco.300-101.v2020-01-06.q78/No.77: You have been asked to evaluate how EIGRP is functioning in a customer network. (Exhibit) Which key chain

Cisco.300-101.v2020-01-06.q78/No.77: You have been asked to evaluate how EIGRP is functioning in a customer network. (Exhibit) Which key chain